I’m wondering if the IP address obtained through a ping is the same as the one required for setting the scope of the Windows firewall rules. The firewall rule is configured to block all outbound traffic to any IP address and applies to all programs and protocols.
Here’s the rule setup:
Type: Outbound Rules
Action: Block the connection
Programs: All
Protocols: Any
Advanced > Profiles: Domain, Private & Public
Scope > Local: Any IP Address
Scope > Remote: Any IP Address
The rule is set for the Domain, Private, and Public profiles and has a local and remote scope of “Any IP Address.”
However, when I ping the target machine that I intend to block, the IP address obtained is accurate:
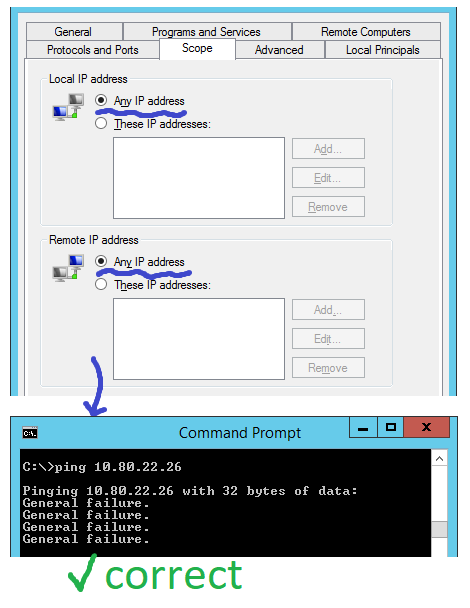
Nonetheless, I do not wish to obstruct all IP addresses; rather, I intend to prohibit only a particular one. But when I modify the rule and alter the scope from “Any” to “These IP addresses,” the traffic somehow manages to bypass the restriction:
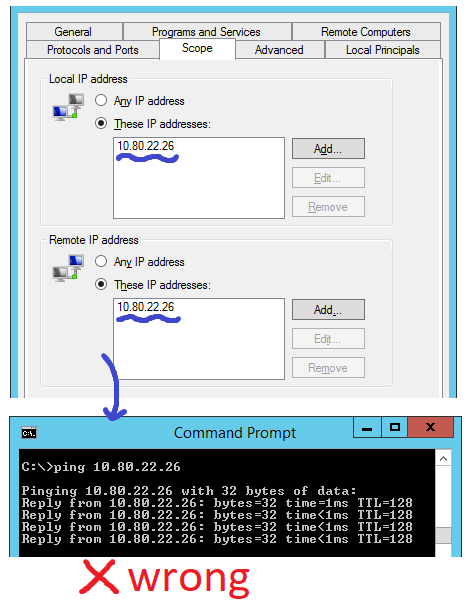
For any diagnostic reasons, here’s the ipconfig from server I want to block:
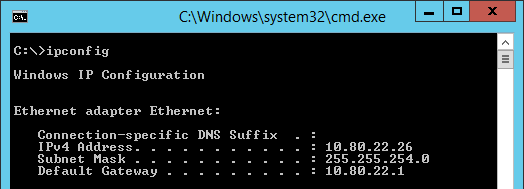
I came across a discussion advising to modify the “Local IP address” value to “Any IP” to impose a block, but I think this is too broad of a scope.
Is there a way to identify the precise local IP addresses that require blocking?
Otherwise, why does restricting all local IP addresses enable the blockage of remote addresses?
3 Answers
Using Windows Firewall to Block IP Addresses on Windows 10
Windows Firewall is a built-in security feature in Windows that helps protect your computer from unauthorized access. It monitors the inbound and outbound traffic of your computer and blocks any suspicious activity. One of the ways to enhance the security of your computer is to block IP addresses that are known to be malicious or suspicious. In this blog post, we will discuss how to use Windows Firewall to block IP addresses on Windows 10.
Understanding IP Addresses
Before we proceed, let’s first understand what an IP address is. An IP address is a unique identifier that is assigned to each device connected to a network. It is used to identify the source and destination of network traffic. IP addresses can be of two types: IPv4 and IPv6. IPv4 addresses are 32-bit numbers that are represented in decimal format, while IPv6 addresses are 128-bit numbers that are represented in hexadecimal format.
When you want to block an IP address, it is important to know the exact IP address that you want to block. You can obtain the IP address of a device by using the ping command in the Command Prompt. The ping command sends a packet of data to the specified IP address and waits for a response. If the device responds, it means that the IP address is valid and active.
Blocking IP Addresses Using Windows Firewall
Now that we know how to obtain an IP address, let’s discuss how to block it using Windows Firewall. Windows Firewall allows you to create inbound and outbound rules that can be used to block or allow traffic based on specific criteria. Here’s how you can create a rule to block outbound traffic to a specific IP address:
1. Open Windows Firewall by typing “Windows Firewall” in the search bar and clicking on “Windows Defender Firewall.”
2. Click on “Advanced settings” on the left-hand side of the window.
3. Click on “Outbound Rules” on the left-hand side of the window.
4. Click on “New Rule” on the right-hand side of the window.
5. Select “Custom” and click on “Next.”
6. Select “All programs” and click on “Next.”
7. Select “Protocol type” and “TCP” and click on “Next.”
8. Select “These IP addresses” and enter the IP address that you want to block. You can also enter a range of IP addresses if you want to block a range of addresses.
9. Select “Block the connection” and click on “Next.”
10. Check all the boxes for the network types that you want the rule to apply to (Domain, Private, Public) and click on “Next.”
11. Name the rule and click on “Finish.”
Once you have created the rule, it will be applied to all outbound traffic from your computer to the specified IP address. If you want to modify the rule or delete it, you can do so by going back to the Windows Firewall settings and selecting the rule from the list of rules.
Identifying the Precise Local IP Addresses That Require Blocking
In some cases, you may want to block specific local IP addresses instead of all local IP addresses. Local IP addresses are the IP addresses that are assigned to devices on your local network. To identify the precise local IP addresses that require blocking, you can use the following steps:
1. Open the Command Prompt by typing “cmd” in the search bar and clicking on “Command Prompt.”
2. Type “ipconfig” and press Enter.
3. Look for the “IPv4 Address” or “IPv6 Address” under the network adapter that you want to block. This is the local IP address of the device.
4. Note down the local IP address and use it to create a rule in Windows Firewall.
By using the local IP address instead of “Any IP address,” you can block specific devices on your network from accessing the internet or other devices on the network.
Conclusion
Windows Firewall is a powerful tool that can help protect your computer from unauthorized access. By blocking IP addresses that are known to be malicious or suspicious, you can enhance the security of your computer and prevent cyber attacks. In this blog post, we discussed how to use Windows Firewall to block IP addresses on Windows 10. We also discussed how to identify the precise local IP addresses that require blocking. By following these steps, you can ensure that your computer is secure and protected from cyber threats.
To block a specific IP address using the Windows Firewall on Windows 10, you can follow these steps:
- Open the Start menu and type “Windows Firewall” in the search bar. Click on the “Windows Defender Firewall” option that appears.
- In the Windows Defender Firewall window, click on “Advanced settings” on the left side of the screen.
- In the Advanced Settings window, click on “Outbound Rules” on the left side of the screen.
- Click on the “New Rule” button on the right side of the screen.
- In the New Outbound Rule Wizard, select “Custom” under “Rule Type” and click “Next”.
- Under “Program”, select “All programs” and click “Next”.
- Under “Protocol and Ports”, select “Any” for both “Protocol type” and “Local port”. Click “Next”.
- Under “Scope”, select “These IP addresses” for “Remote IP address”. Click “Add” and enter the specific IP address that you want to block in the “Add IP Address” window. Click “OK” to add the IP address.
- Under “Action”, select “Block the connection” and click “Next”.
- Under “Profile”, select the network profiles that you want the rule to apply to (e.g. Domain, Private, Public). Click “Next”.
- Give the rule a name and optional description, then click “Finish” to create the rule.
By following these steps, you should be able to create a firewall rule that blocks the specific IP address that you want to block.
As for the difference between the IP address returned via a ping and the one that you need to enter when setting the scope of the firewall rule, the ping command is used to test the connectivity between two devices on a network. The IP address that is returned via a ping is the IP address of the device that you are pinging. This may or may not be the same as the IP address that you need to enter when setting the scope of a firewall rule.
For example, if you are trying to block access to a device on your local network, you will need to enter the local IP address of that device in the firewall rule. This can be determined by using the “ipconfig” command on the device that you want to block, as you have done. Alternatively, you can use the “arp -a” command on the local device to view the IP address and MAC address of devices on the local network.
On the other hand, if you are trying to block access to a device on a remote network, you will need to enter the public IP address of that device in the firewall rule. This can be determined by using a website that shows your public IP address, such as whatismyip.com.
I hope this helps! Let me know if you have any other questions.
The Local IP refers to a unique IP address on the particular device on which you are configuring the firewall rule, rather than the IP address of the remote device. It’s feasible to allocate several local IP addresses if multiple services are needed on an IP-mapping function.
In any scenario where you aim to restrict all communication with the remote IP from your device, selecting “any” is necessary for the Local IP configuration.